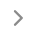Most business owners know passwords alone aren’t enough to keep your data safe. Between 2004 and July 2024, passwords were the most frequently leaked type of data, with two billion user passwords leaked during this period.
To better combat data breaches, more companies are turning to stronger authentication methods, such as multi-factor authentication (MFA), single sign-on (SSO), or two-factor authentication (2FA).
What do all these acronyms mean, and how can you determine which solution is the right fit for your business? In this guide, we’ll break down each approach's core differences, benefits, and security considerations to demonstrate that combining MFA and SSO in a solution like Plivo’s Verify API is best for most businesses.
{{cta-style-1}}
What is single sign-on (SSO)?
Single sign-on (SSO) is a user authentication process that allows someone to log in once with a single set of login credentials and access multiple applications or services without needing to re-enter their username and password for each one.
Think of SSO as a master key that opens many doors—users sign in once and get instant access to all their work tools without having to remember multiple passwords. This approach reduces login headaches and password fatigue, making it easier for users to stay secure and productive.
How does SSO work?
SSO verifies a user’s identity through a centralized system. When the user logs into an SSO portal, the system checks their login credentials. It then generates a token that grants access to various applications within the network, simplifying access management for authorized users.
5 key benefits of SSO & why you should use it
Single sign-on offers several benefits, but here are five key reasons why you should consider using SSO:
- It streamlines the user experience: With SSO, users only need to use one password to log into a dashboard and access all connected applications—no more wasted time juggling multiple logins.
- It reduces password fatigue: Less is more. Fewer passwords mean less mental load, reducing the risk of weak or reused passwords and enhancing security.
- It improves productivity: Imagine the time saved when users can instantly access all the tools they need. This quick access means more focus on tasks and drives efficiency.
- It simplifies centralized management: IT teams can use SSO to manage user access from a single dashboard. It makes onboarding and offboarding new users smooth and hassle-free.
- It lowers help desk costs: Fewer passwords mean fewer forgotten credentials. This leads to a significant drop in password reset requests, reducing the burden on IT support teams and cutting help desk costs.
3 key security risks of SSO you should consider
- It creates a single point of failure: If someone gains access to SSO credentials, they could access multiple services connected together, creating a significant security vulnerability.
- It relies on centralized authentication: If the SSO service experiences downtime or technical issues, users may lose access to all associated applications, causing operational disruptions.
- It becomes an attractive target for cyber attacks: Because SSO systems control access to multiple applications, attackers often target them. A successful breach could expose sensitive data across various systems.
What is multi-factor authentication (MFA)?
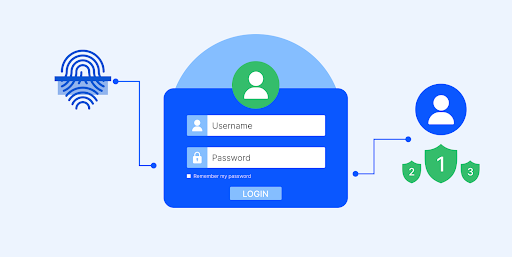
Multi-factor authentication (MFA) requires users to verify their identity using two or more forms, adding multiple layers of defense against unauthorized access. Think of it as a security system with multiple locks; even if someone knows your password, they still need other credentials to log in.
How does MFA work?
A lot of people get confused between 2FA and MFA, but here’s the exact difference:
2FA (two-factor authentication) always requires exactly two forms of verification, usually something you know (like a password) and something you have (like an OTP or security token). On the other hand, MFA covers two or more forms of verification, adding even more layers of security by incorporating things like biometrics (something you are) alongside what you know and have.
Imagine overlapping circles in a Venn diagram—2FA is one circle inside the broader MFA circle, which lets you combine different layers for extra protection.
In implementation, it could look like this: after typing in your password, you might also need to enter a verification code sent to your phone or use a fingerprint scan. This layered approach makes it significantly harder for unauthorized users to gain access to user accounts.
3 key types of authentication factors used in MFA
Authentication factors are the methods used to confirm a user’s identity. In multi-factor authentication (MFA), at least two different factors are required to gain access. Here's a closer look at the types of authentication factors:
1. Knowledge factors (something you know):
These are login credentials that only the user knows, such as passwords, PINs, or answers to security questions. Knowledge factors are the most common type of authentication but are also considered the least secure due to the risk of being guessed or stolen through phishing attacks.
2. Possession factors (something you have):
These involve something the user physically possesses, like a smartphone, security token, or smart card. Possession factors are generally more secure than knowledge factors because they require an additional physical item that attackers would need to acquire. Common examples include SMS codes sent to a user’s mobile device or authentication apps like Google Authenticator.
3. Inherence factors (something you are):
These are biological traits unique to the user, such as fingerprints, facial recognition, voice recognition, or retina scans. Inherence factors provide a high level of security because they are unique to each individual and are difficult to replicate. This type of factor is commonly used in high-security environments, such as government agencies or financial institutions.
By using multiple authentication factors, MFA creates a layered defense, making it more challenging for attackers to gain unauthorized access.
5 benefits of MFA & why you should use it
Here are five important benefits for businesses thinking about using MFA.
- It enhances security. MFA adds multiple layers of security by requiring more than one form of verification, significantly reducing the risk of unauthorized access even if one credential is compromised.
- It protects against credential theft. Since MFA provides multiple authentication layers, even if a password is stolen, additional factors like a biometric scan or a verification code sent to a mobile device make it much harder for attackers to gain access.
- It helps comply with regulatory requirements. Many industries have regulations that require strong authentication methods. Implementing MFA helps businesses comply with PCI DSS, GDPR, and HIPAA standards.
- It reduces the risk of data breaches. By adding extra security layers, MFA helps prevent data breaches, which can save the business from costly fines and reputational damage.
- It improves user trust. Users feel more secure knowing that their accounts and data are protected by multiple layers of authentication, enhancing trust in the organization.
Security risks of MFA
- It can pose usability challenges. MFA can sometimes make the login process more cumbersome, potentially leading to user frustration or reduced productivity if not implemented carefully.
- It is vulnerable to phishing and social engineering attacks. Attackers might still use sophisticated phishing tactics to trick users into providing all required authentication factors, bypassing the additional security layers.
- It relies on secondary factors that can be compromised. If secondary authentication methods (like SMS-based codes) are compromised through SIM swapping or interception, attackers could still gain access despite MFA.
SSO vs MFA: the main differences
Here are five core differences between MFA and SSO:
- Different goals: MFA enhances security by requiring multiple authentication factors to verify a user's identity. SSO focuses on convenience by allowing access to multiple applications with a single set of credentials; instead of remembering multiple usernames, users can easily sign in once and access all authorized applications they need.
- Security vs. convenience: MFA offers stronger protection by requiring multiple authentication methods. SSO, on the other hand, focuses on user convenience, which can lead to vulnerabilities if credentials are compromised.
- User experience: SSO simplifies the login process and reduces password fatigue. Meanwhile, MFA adds extra steps, which can feel like a hassle to some users but adds extra layers of security.
- Setup complexity: Setting up MFA involves integrating various authentication methods, which can be complex. SSO requires connecting different applications to one central login, which simplifies user access but can be tricky if not done right.
- Risk management: MFA minimizes the risk of unauthorized access with extra verification layers, while SSO simplifies access control but can become a single point of failure if hacked.
Both SSO and MFA have their place in your security scheme, depending on what’s more important for your business—security or convenience.
SSO vs. 2FA vs. MFA
When securing access to your systems, understanding the differences between SSO, 2FA, and MFA is crucial. Each method can impact your organization’s security, budget, and user experience. Let’s dive into how these authentication methods compare across key factors.
Cost implications
Implementing MFA or 2FA might involve additional costs due to the need for specialized software or hardware (like biometric scanners or security tokens). SSO solutions can reduce password and user support costs but may require investment in a robust identity management system.
Impact on user experience
SSO enhances user experience by reducing the required logins, while MFA and 2FA may introduce additional steps but offer stronger security. The choice depends on balancing convenience against security measures.
Implications for businesses
Businesses need to consider the nature of their operations, regulatory requirements, and user base when deciding on an authentication method. While MFA offers the highest security, SSO can greatly improve productivity and user satisfaction.
4 important things for selecting the right provider for your organization
If you’re looking for an authentication solution for your business, here are the key things you should consider:
1. Security needs and compliance requirements
To begin with, consider the sensitivity of the data your organization handles and any regulatory requirements, like GDPR, HIPAA, or PCI DSS, that might mandate specific authentication methods. For high-security environments, a combination of SSO with MFA can provide a balanced approach.
With Plivo, you get built-in compliance features that help you adhere to regulations without adding extra costs. Plivo's Fraud Shield, for example, protects against SMS pumping fraud, ensuring your authentication processes remain secure and compliant.
{{cta-style-1}}
2. User experience and usability
Your authentication method should strike the right balance between security and ease of use, and seamless integration with your current IT infrastructure is key. Plivo simplifies this by offering a reliable OTP solution that integrates effortlessly with your systems, ensuring users get their OTPs when they need them.
Whether you're using OTPs as part of a 2FA or MFA setup, Plivo guarantees 99.99% uptime, so users never miss a beat. With support for WhatsApp, SMS, and voice call, Plivo provides flexible, secure options to meet your authentication needs without disrupting your existing workflows.

3. Cost and budget constraints
It’s important to understand the total cost of ownership for your authentication solution, including all associated fees.
Plivo offers a cost-effective approach: you only pay for the SMS and voice services you use, not for authentication fees. Plus, with Plivo’s pre-registered phone numbers and no monthly rental fees, you can keep operational costs low and predictable.

4. Scalability and flexibility
As your organization grows, your authentication solution should scale with you, accommodating more users, devices, and applications without a hitch.
Plivo’s solutions are designed to be scalable, supporting global delivery and providing real-time delivery reports so you can track and optimize performance as your needs evolve.
Simplify your MFA rollout with Plivo
Whether you're securing internal systems or protecting customer data, SSO and MFA are crucial for your business. SSO simplifies user access, reducing password fatigue and enhancing user experience, while MFA provides robust protection against unauthorized access by requiring multiple authentication steps.
In today’s digital world, combining SSO with MFA offers the best of both worlds—convenience and robust security. Providers like Plivo make it easy to set up and integrate both, helping you protect your data without sacrificing user experience.